The term “virtual private network” refers to the ability to create a secure network connection while using public networks. VPNs encrypt your internet traffic and hide your true identity on the internet. Third parties will have a harder time tracking your online activities and stealing data as a result of this. The encryption is carried out in real-time.
It’s used to get around geo-blocks as well as for security. It is a safe and secure way to share files, communicate, and access data remotely without the risk of being hacked.
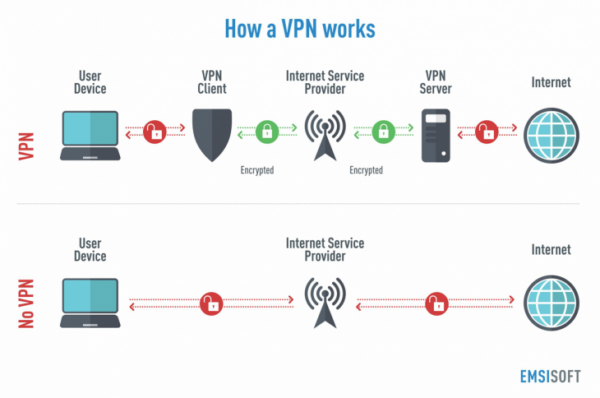
How does a virtual private network (VPN) work?
A VPN masks your IP address by allowing the network to route it through a VPN host’s specially configured remote server. This means that when you use a VPN to access the internet, the VPN server becomes one’s data source. This means that your Internet Service Provider (ISP) and other third parties will be unable to see which websites you visit or the data you send and receive over the internet. A VPN acts as a filter, converting all of your data into gibberish. Even if someone managed to obtain your information, it would be useless.
The history of virtual private networks
There has been a movement to protect and encrypt internet browser data since humans began using the internet. Back in the 1960s, the US Department of Defense was involved in projects aimed at encrypting internet communication data.
The VPN’s forerunners were
Their attempts resulted in the development of ARPANET (Advanced Research Projects Agency Network), a packet switching network, and the Transfer Control Protocol/Internet Protocol (TCP/IP).
Link, internet, transport, and application were the four levels of TCP/IP. Local networks and devices could be connected to the universal network via the internet, and this is where the risk of exposure became apparent. In 1993, a team from Columbia University and AT&T Bell Labs succeeded in developing swIPe: Software IP Encryption Protocol, which was the first version of the modern VPN.
Wei Xu created the IPSec network the next year, which is an internet security protocol that authenticates and encrypts data packets shared over the internet. Gurdeep Singh-Pall, a Microsoft employee, created the Peer-to-Peer Tunneling Protocol (PPTP) in 1996.
Early VPNs
The internet was growing in popularity at the same time that Singh-Pall was developing PPTP, necessitating the development of consumer-ready, sophisticated security systems. Anti-virus software was already effective at reducing malware and spyware from infecting a computer system at the time. People and businesses, on the other hand, began to demand encryption software that would allow them to hide their internet browsing history.
As a result, the first VPNs appeared in the early 2000s, but they were almost exclusively used by businesses. However, the consumer market for VPNs began to pick up after a rash of security breaches, particularly in the early 2010s.
VPNs and their current application
The number of VPN users worldwide increased more than fourfold between 2016 and 2018 as stated by GlobalWebIndex. One in every five internet users in countries like Thailand, Indonesia, and China, where internet use is restricted and censored, uses a VPN. The percentage of VPN users in the United States, the United Kingdom, and Germany is around 5%, but it is growing.
The increasing demand for content with geographical access restrictions has been one of the biggest drivers for VPN adoption in recent years. For instance, digital platforms like Netflix and YouTube restrict access to certain videos to specific countries.
Kind of VPNs
There are many different types of VPNs, but there are three main types that you should be familiar with:
- SSL VPN
Not all company employees have access to a company laptop that they can use to work from home. Many companies faced the problem of not having enough equipment for their employees during the corona crisis in the Spring of 2020. Using a personal device (PC, laptop, tablet, or phone) is frequently used in these situations. In this case, businesses rely on an SSL-VPN solution, which is typically implemented through a dedicated hardware box.
- Site-to-site VPN
A site-to-site VPN is essentially a private network designed to conceal private intranets while allowing users of these secure networks to share resources. If your company has multiple locations, each with its local area network (LAN) connected to the WAN (Wide Area Network), a site-to-site VPN is useful there. Site-to-site VPNs are also useful if you have two separate intranets and want to send files between them without requiring users from one intranet to access the other.
Large corporations are the primary users of site-to-site VPNs. They are difficult to set up and do not provide the same level of flexibility as SSL VPNs. They are, however, the most efficient method of ensuring communication within and between large departments.
- Client-to-Server VPN
Using a VPN client is similar to using an extension cable to connect your home PC to the company. Employees can use the secure connection to connect to the company network from their home office and act as if they were in the office. A VPN client must, however, be installed and configured on the computer first.
The user establishes a direct connection to the internet through his/her VPN provider rather than through his/her ISP. This essentially cuts the VPN journey’s tunnel phase in half. Instead of creating an encryption tunnel to mask an existing internet connection, the VPN can automatically encrypt data before making it available to the user.
Greater efficiency and universal access to company resources are two benefits of using a VPN connection. If a suitable phone system is available, the employee can, for example, use a headset to connect to the system and pretend to be at their place of business. Customers of the company have no way of knowing whether the employee is working in the office or at home.
Benefits of a VPN connection
- A VPN connection hides your online data traffic and protects it from prying eyes. Anyone with network access and a desire to see unencrypted data can do so. Hackers and cybercriminals are unable to decipher this data when using a VPN.
- Secure encryption: An encryption key is required to read the data. In the event of a brute force attack, a computer would take millions of years to decipher the code without one. Even on public networks, your online activities are hidden with the help of a VPN.
- Disguising your location: VPN servers serve as proxies for you on the internet. Your exact location cannot be determined because the demographic location data comes from a server in another country. Furthermore, most VPN services do not keep track of your activities. Some providers, on the other hand, keep track of your actions but do not share them with third parties. This means that any possible record of your user behavior will be permanently erased.
- Access to regional web content: Access to regional web content is not always available from all locations. Content on services and websites is frequently restricted to certain regions of the globe. To determine your location, standard connections use local servers in the country. This means you won’t be able to access content from your home while on the road, and you won’t be able to access international content from your home. With VPN location spoofing, you can change your location by connecting to a server in another country.
- Secure data transfer: You may need to access important files on your company’s network if you work remotely. This type of data necessitates a secure connection for security reasons. A VPN connection is frequently required to gain access to the network. To reduce the risk of data leakage, VPN services connect to private servers and use encryption methods.
VPN’s Disadvantages
- When data is fetched through a VPN, the time it takes to fetch the data can sometimes increase indicating that there may be a performance issue in terms of time
- VPN allows you to hide your identity but your VPN provider company may steal your data posing a security risk
- When a VPN connection is lost, the IP address used to establish the connection may be revealed to the network from which the connection was established
- Using a VPN to get around a website’s restrictions is rarely possible
Why should you use a virtual private network (VPN)?
When you connect to the internet your ISP usually sets up your connection. It uses your IP address to track you. Your network traffic is routed through the servers of your Internet service provider, who can log and display everything you do online.
Although your Internet service provider may appear to be trustworthy, it may share your browsing history with advertisers, the police or government, and/or other third parties. Cybercriminals can also target ISPs, compromising your personal and private information if they are hacked.
This is particularly necessary if you use public Wi-Fi networks frequently. You never know who is watching your online activities or what they might steal from you, such as passwords, personal information, payment information, or even your entire identity.
One or more tasks should be delegated to your VPN. It’s also a good idea to keep the VPN itself secure. A comprehensive VPN solution should include the following features:
- IP address encryption: A VPN’s main function is to hide your IP address from your ISP and other third parties. This allows you to send and receive information over the internet without fear of it being seen by anyone other than you and your VPN provider.
- Protocol encryption: A VPN should also prevent you from leaving traces, such as your browsing history, search history, and cookies. Cookies’ encryption is particularly important because it prevents third parties from gaining access to sensitive data such as personal information, financial information, and other website content.
- Kill Switch: If your VPN connection is suddenly terminated, your secure connection will be terminated as well. A good VPN can detect this unexpected downtime and shut down pre-selected programs, lowering the risk of data compromise.
- Two-factor authentication: A strong VPN checks everyone who tries to log in using a variety of authentication methods. For example, you may be asked to enter a passwordbefore receiving a code on your mobile device. Uninvited third parties will have a hard time accessing your secure connection as a result of this.
Past Incidents
In the year 2020, Seven VPN providers that claim to keep no logs of their users’ online activities recently exposed 1.2 terabytes of private user data to anyone looking. The data included the Personally Identifiable Information (PII) of up to 20 million VPN users, which was discovered on a server shared by the services. UFO VPN, FAST VPN, FREE VPN, SUPER VPN, Flash VPN, Secure VPN, and Rabbit VPN are all implicated in the incident.
Recent Incident
According to an investigation into a ransomware attack on Japanese video game developer Capcom, malicious hackers gained access to the company’s servers via an outdated virtual private network (VPN).
The attack took place in November 2020, as previously reported by The Daily Swig, when malicious hackers took down email and file servers. According to a third-party investigation, the unknown actors gained access to networks in both the United States and Japan by exploiting the VPN service, which Capcom claimed was still in use due to Covid-19 “burdens.”
According to the post-mortem report released on April 13, 2021 the VPN was used by staff from Capcom USA, Inc., the developer’s North American subsidiary
Also Read:
INTERNATIONAL DAY OF REFLECTION ON THE 1994 GENOCIDE IN RWANDA – April 7
World Autism Awareness Day (WAAD) 2021
Good Friday 2021: Know The Significance here!
Get Free Online Test Series, GK updates in form of Beepedia, BeeBooster, as well as latest updates for Bank PO, Bank Clerk, SSC, RBI, NABARD, and Other Government Jobs.
.















