Question
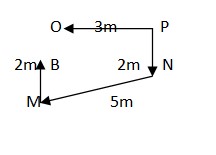
What is the direction of B with respect to
O? Study the given information carefully and answer the given questions below it: O is 3m to the West of P, who is facing north direction. N is 2m South of P. M is 5m South-West of N. B is 2m to the North of M.Solution
- Who is the Managing director of IMF?
Programming language Java was developed by________.
What is the name of the IRDAI portal designed to streamline insurance services?
The British East India Company captured Pondicherry (Puducherry) from the French in the year ______.
NITI Aayog has constructed the SDG India Index spanning across 13 out of 17 SDGs as prescribed by UNO. Which of the following SDG goals of UNO is left o...
Which of the following committee had recommended the consolidation of banks -:
Under the United Nations Convention on the Law of the Sea (UNCLOS), coastal states are granted sovereign rights for the purpose of exploring, exploiting...
Mughal miniature painting reached its peak during the rule of _____
Which of the following states won the ‘Best Tableau’ award at the 71st Republic Day parade in January 2020?
In September 2020, which of the three bills was passed by the parliament aimed at transforming agriculture in the country and raising farmer’s income?...
Relevant for Exams:



