Question
Two workers A and B were put to some work. If A worked
alone, he would have taken 8 hours more than when both A and B had worked together. If B worked alone, he would have taken 4(1/2) hours more than when both A and B had worked together. In how much time will both of them together complete the work?Solution
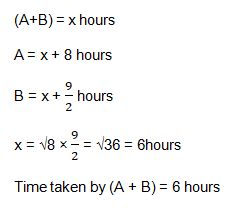
'A', 'B' and 'C' started a business together such that 'A' invested a 25% of the total capital invested by 'A', 'B' and 'C' together, 'B' invested 40% o...
Radha started a dairy farm by investing Rs. 80,000. After 4 months, Krishna joined her, contributing Rs. 1,20,000 to the investment. At the end of one y...
A and B together start a business with investment of Rs. 2100 and Rs. (x + 800), respectively. If the profit earned after 5 years is Rs. 7000 and share ...
‘A’, ‘B’ and ‘C’ started a business by investing Rs. 5,000, Rs. 6,000 and Rs. 4,000, respectively. After 6 months, ‘B’ decreased his inv...
Together, 'P' and 'Q' invested Rs. 16,000 and Rs. 24,000 to launch their firm. After 'Q' departed after four months, 'R' joined 'P' by contributing Rs. ...
Ajay and Vijay started a business with investments of Rs. 25,000 and Rs. 15,000, respectively. After 9 months, Sanjay joined them with an investment equ...
P started a business with an investment of Rs.10000, after 6 months Q joined him with Rs.12000 and after another 6 months R joined them with Rs.15000. I...
Ayush, Tarun and Chintu started a business with initial investments in the ratio 4:5:7, respectively. After one year Ayush, Tarun and Chintu made additi...
- ‘D’ started a business by investing Rs. 1,600. Seven months later, ‘E’ joined him by investing 50% of D’s capital. If total profit after one year...
The sum of the incomes of 'G', 'H', and 'I' is Rs. 18000. 'G', 'H', and 'I' spend 70%, 65%, and 85% of their respective incomes, with their savings in t...



