Question
Fill in the blank with the appropriate
word. Fill in the blanks with the most appropriate word given in the options against the correct blank number. The Department of Biotechnology has issued guidelines ____________ (89) norms for research into genetically modified crops and ____________ (90) challenges of using foreign genes to change crops profile. The ‘Guidelines for Safety Assessment of Genome Edited Plants, 2022’ exempt researchers who use gene-editing technology to modify the genome of the plant from ___________ (91) approvals from the Genetic Engineering Appraisal Committee (GEAC), an expert body of the Environment Ministry. The GEAC ___________ (92) research into GM plants and recommends, or disapproves, their release into farmer fields. The final call however is taken by the Environment Minister as well as States where such plants could be cultivated. The Environment Ministry too has ___________ (93) this exemption.Solution
Here, ‘evaluates’ is the correct word. Other words are inappropriate.
Who has written the novel ‘Ajay to Yogi Adityanath’?
Which one of the following is not an iron ore?
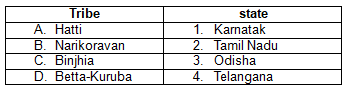
Consider the following pairs:
Which NBFCs are now allowed to co-lend with private lenders under RBI’s 2025 Co-Lending Arrangement reforms?
According to a joint report by India Cellular & Electronics Association (ICEA) and Accenture, what is the estimated revenue potential that circular busi...
Which tribal community celebrates the festival called Sohrai, derived from the paleolithic age word 'soro'?
In which year was Raj Bhavan established in Nainital?
Regarding the National Human Rights Commission (NHRC), consider the following statements:
1.The NHRC investigates complaints related to human rig...
India recently won the 2024 ICC T20 World Cup for the second time. In which year did India first win the ICC T20 World Cup?
'Mukhyamantri Ladli Behna Awas Yojana' has been launched in which state?
Relevant for Exams:



