Question
Which of the following statements regarding the system
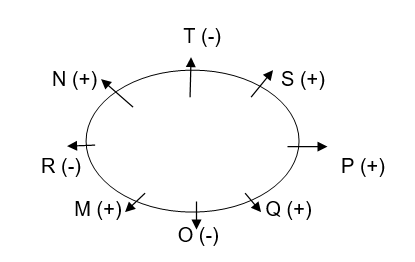
is wrong? Carefully read the given information and answer the given questions. The 8 people sitting on the outside of the M, N, O, P, Q, R, S and T sculptors are sitting outside (not necessarily in the same order) in such a way that there is a uniform distance between each of them. There are 5 men and 3 women. No two women are sitting together. i) M, which is a man, is sitting opposite S. ii) T and N are neighbors. iii) N is sitting on the third place from the right of O, which is a woman. iv) M is neither neighbour of N, nor is N the neighbor of any male v) A person is sitting between S and N. vi) P is not a neighbor of M but sitting in front of R.Solution
The President of India is elected indirectly by the electoral college consisting of the elected members of the:
Which of the following provisions has been newly introduced under BNSS, 2023 to promote the use of technology in criminal procedure?
Among the following which section deals with the admissibility of Evidence shall be decided by the Judge_____
The power of superintendence over CBI in corruption cases was judicially recognized in:
A wishes to prove, by secondary evidence, the contents of a lost document.
Consider the following statements regarding Evidence Act applicability in PMLA proceedings:
Statement 1: Hearsay evidence is admissible in PMLA...
The Vigilance Commissioner may act as the Central Vigilance Commissioner when the office of CVC is vacant as per:
'la principle de legalite' means:
What conditions must be met for the Authority to grant a certificate of registration to an applicant to operate as an insurer under the Insurance Act?
Are official communications protected under the Indian Evidence Act, 1872? If yes, under which section?
Relevant for Exams:



