Question
Which of the following combination is
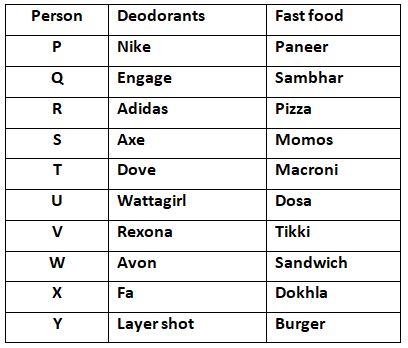
true? Directions (Q.116-120): Study the following information carefully and answer the following questions given below: Ten persons P, Q, R, S, T, U, V, W, X and Y like different deodorants, viz. Engage, Nike, Adidas, Axe and Dove, Wattagirl, Rexona, Avon, Fa and Layer shot. All of them eat a different fast foods, viz. Pizza, Momos, Macroni, Dosa, Sambhar, Paneer, Tikki, Sandwich, Dokhla and Burger but not necessarily in the same order. (i) The one who likes Layer shot eats Burger. (ii) X does not like Nike or Layer shot. (iii) S likes Axe and eats Momos. (iv) U eats Dosa and likes Wattagirl. (v) W eats Sandwich. (vi) The one who eats Pizza likes Adidas. (vii) P eats Paneer and X eats Dokhla. (viii) V likes Rexona. (ix) Neither P nor Q likes Fa. (x) P does not like Engage. (xi) R likes Adidas and W likes Avon. (xii) T likes Dove and eats Macroni. (xiii) Q eats Sambhar.Solution
Ravi and Rekha, alone can complete a work in 25 days and 50 days, respectively. They started the work together and left after 10 days such that the rema...
A alone can finish a piece of work in 10 days and B alone can finish it in 15 days. They work together for 3 days and the remaining work is finished by ...
P, Q & R can finish a work in 10 days, 15 days, and 20 days, respectively, working alone. P and Q work on the first day, P and R work on the second day,...
(x + 6) workers complete 40% of a job in 8 days by working 5 hours/day. The remaining work is done by (x + 2) workers in 16 days working 5 hours/day. Fi...
Amin, Basha and Cheez can do a piece of work in 90, 40 and 12 days respectively. But they decide. That a single person will work in a day and receive Rs...
138 unit of work can be completed by P alone in 23 days. P started working alone and joined by Q after 11 days such that they completed the remaining wo...
- Two workers, A and B, can finish a task in 36 days and 48 days respectively, working alone. How many days will they take to complete the work together?
- Pipes X and Y can fill a tank in 45 minutes and 60 minutes respectively. Another pipe Z can empty the tank in 1 hour 30 minutes. If X and Z are opened firs...
8 men working 6 hours a day can complete a piece of work in 6 days. If efficiency of each woman is 20% more than that of each man, then how many women w...
- Alok finishes 60% of a project in 30 days, while Neha finishes 20% of the same in 15 days. Alok worked for 25 days and then stopped. Find the time taken by...



