Question
How many boxes are kept between V and the box which is
kept immediately below box U? Study the following information carefully and answer the question given below: Nine boxes viz. S, T, U, V, W, X, Y, Z and R are kept one above another but not in the same order. The box kept at the bottommost position is numbered as 1 and the box kept at the topmost position is numbered as 9. At most two boxes are kept below box U. Three boxes are kept between R and the box which is kept immediately above box U. W is kept two boxes above box R. Two boxes are kept between W and S. Box Z is kept immediately below box X. Box Y is kept three boxes below box X. Box T is kept above box V.Solution
We Have, At most two boxes are kept below box U. Three boxes are kept between R and the box which is kept immediately above box U. 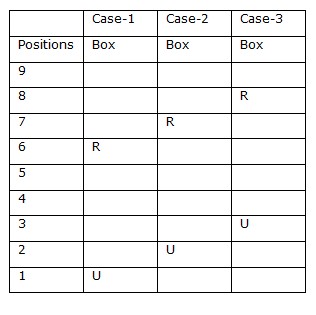 Again we have, W is kept two boxes above box R. Two boxes are kept between W and S.
Again we have, W is kept two boxes above box R. Two boxes are kept between W and S. 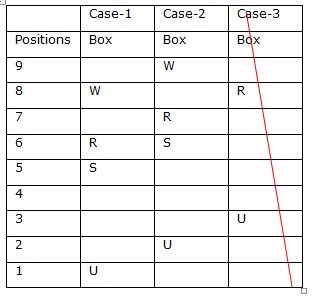 Case-III gets eliminated because no space left for W. Again we have, Box Z is kept immediately below box X. Box Y is kept three boxes below box X. Box T is kept above box V. Case-I gets eliminated because no space left for X and Y. So final arrangement is Case-2
Case-III gets eliminated because no space left for W. Again we have, Box Z is kept immediately below box X. Box Y is kept three boxes below box X. Box T is kept above box V. Case-I gets eliminated because no space left for X and Y. So final arrangement is Case-2 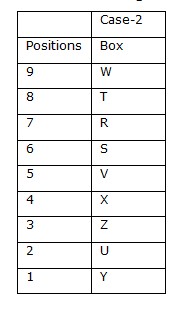
Scientific name of green gram is:
A solution contains 1/ 10000 moles/I H+ ions. What is the concentration of hydroxyl ions in this solution?
Who discovered the nematicidal properties of Ethylene Di bromide (EDB)?
Government of India announce MSP on the recommendation of
Principal acid found in apples
Stomata are regulated by:
Which among the following insect causes damage inside the stem
The tip clipping of infested seedling to manage stem borer in rice is a
Which crop is known as Drosophila of crop plants?
homozygous population includes
Relevant for Exams:



