Question
If C is related to A, D is related to E, in the same way
to how G is related to? Study the following information carefully and answer the question below: There are seven boxes, namely A, B, C, D, E, G and H. All of them are placed in a stack one above the another but not necessarily in the same order. Only one box is placed in between A and H. Three boxes are placed between G and A. Two boxes are there in between H and B. Only one box is in between B and E. D is not placed immediately before or immediately after the box H. C is placed immediately above box D. G is placed before box A.Solution
We are given with the following information, Three boxes are kept between G and A. G is kept one of the box before A. Only one box is placed between A and H .Two boxes are between H and B. If box G is placed on the top then A is placed at 3rd position from the bottom of the stack. 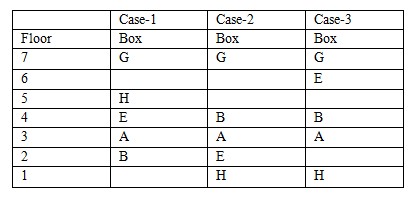 Only one box is kept between B and E. Box D is not kept immediately before or immediately after the box H. C is placed immediately above D. According to the given information, D cannot be placed immediately before or after H and box C is kept just before box D. CASE 1 AND CASE 3 got eliminated because C and D are kept together, which is not possible in both these case. So the final arrangement is:
Only one box is kept between B and E. Box D is not kept immediately before or immediately after the box H. C is placed immediately above D. According to the given information, D cannot be placed immediately before or after H and box C is kept just before box D. CASE 1 AND CASE 3 got eliminated because C and D are kept together, which is not possible in both these case. So the final arrangement is: 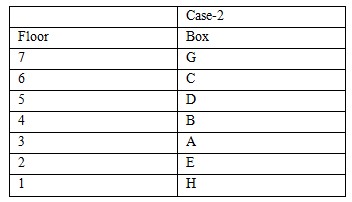
What does the "Model" represent in the MVC architecture?
Consider below arithmetic operation in python and predict the output
X=7.5
Y=2
print(X//Y)
Which scheduling policy may result in high waiting times for long-running jobs?
Which data analytics technique is suitable for handling missing data points in a dataset?
Which device operates at the Data Link Layer of the OSI model?
Which is the first process launched by the LINUX?
Which protocol is used for secure remote shell access and file transfers?
Which sorting algorithm is known for its best-case time complexity of O(n) when the input is already partially sorted?
C++ follows ___.
Which command is used to delete a file in a Unix/Linux system?



