Question
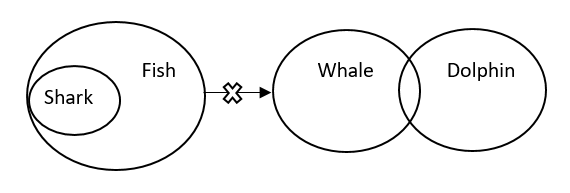
Statements: All Shark are Fish. No Fish
is a Whale. Some Whale are Dolphin. Conclusion: Some Whale are Sharks is a possibility. All Dolphin can be Fish. In the question below there are three statements followed by two conclusions I and II. You have to take the three given statements to be true even if they seem to be at variance from commonly known facts and then decide which of the given conclusions logically follows from the three statements disregarding commonly known facts.Solution
Eight people are sitting in two parallel rows containing 4 people each in such a way that there is equal distance between adjacent persons. In row 1, D,...
Select the wrong term in the following number series:
9, 10, 19, 44, 93, 175
Four letter-clusters have been given, out of which three are alike in some manner and one is different. Select the one that is different.
Four of the following five are somehow similar and therefore create a group. Which of these is not related to this group?
BFJ, MQU, KPU, JNR, LPT
Select the option that is related to the third term in the same way as the second term is related to the first term.
Typhoid : Bacteria :: Influenza : ?
There is a family of six members. There are two married couples. X is a daughter of F, who has two children. F is the mother of Y. Y is the husband of ...
Six people C, D, E, K, L and M are each of a different height. E is shorter than only L. Only one person is shorter than C. K is shorter than D but tall...
Select the number from among the given options that can replace the question mark (?) in the following series.
612 615 621 630 642 ?
Three of the following pairs of letters follow a certain rule/logic/relation and hence are alike in a certain way. Select the incongruous one from the g...
Statements:
All notebooks are stationeries.
Some stationeries are pencils.
All pencils are costly.
Conclusions:
I...



