Question
Seven boxes viz. S, T, U, V, W, X and Y are kept one
above other in the form of stack. How many boxes are kept above box W? I. Only two boxes are kept between box T and box X. Only three boxes are kept above box V. Box T and V are kept together. Only one box is kept between box W and box Y. Box S is neither kept at bottom nor adjacent to box T. II. Box U is kept second from top. Box W is kept at any place above box Y. Only three boxes are kept between box X and box U. Box V, which is neither kept adjacent to box U nor box X, which is kept at s gap of two box from S. Box T doesn’t kept adjacent to box X but kept at any place below box S. Each of the questions below consists of a question and two statements numbered I and II given below it. You have to decide whether the data provided in the statements are sufficient to answer the question:Solution
From I: We have: Only three boxes are kept above box V. Box T and V are kept together. Only two boxes are kept between box T and box X Only one box is kept between box W and box Y. Box S is neither kept at bottom nor adjacent to box T, that means box S is kept at top and box X is kept below box T. Based on above given information we have: 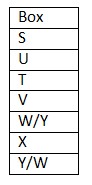 Clearly, we don’t know exact position of box W. Hence, statement I is not sufficient. From II: We have: Box U is kept second from top. Only three boxes are kept between box X and box U, that means box X is kept second from bottom. Box V, which is neither kept adjacent to box U nor box X, which is kept at s gap of two box from S, that means box V is kept fourth from bottom. Box T doesn’t kept adjacent to box X but kept at any place below box S, that means box S is kept at top. Box W is kept at any place above box Y, that means box Y is kept at bottom.
Clearly, we don’t know exact position of box W. Hence, statement I is not sufficient. From II: We have: Box U is kept second from top. Only three boxes are kept between box X and box U, that means box X is kept second from bottom. Box V, which is neither kept adjacent to box U nor box X, which is kept at s gap of two box from S, that means box V is kept fourth from bottom. Box T doesn’t kept adjacent to box X but kept at any place below box S, that means box S is kept at top. Box W is kept at any place above box Y, that means box Y is kept at bottom. 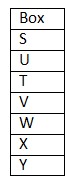 Clearly, only four boxes are kept above box W. Hence, statement II alone is sufficient.
Clearly, only four boxes are kept above box W. Hence, statement II alone is sufficient.
गंगा का पर्यायवाची शब्द नहीं है –
दही बड़ा दो अलग-अलग वस्तुओं का मेल है, इसलिए इसका विग्रह दह...
निम्नलिखित में से किस वाक्य में अशुद्धि नहीं है?
शब्दों का संक्षिप्त रूप लिखने के लिए प्रयुक्त होने वाला च�...
निम्नलिखित में से एक 'पत्थर' का पर्यायवाची नहीं है:
निम्नलिखित प्रश्न में , चार विकल्पों में से , उस सही विकल्प...
जहाँ उपमेय में उपमान की संभावना की जाए, वहाँ कौन-सा अलंकार �...
'अनुग्रह' का उपयुक्त विपरीतार्थक शब्द होगा-
‘सुरेश’ का संधि-विच्छेद क्या है?
निम्नलिखित में से कौन सा वाक्य शुद्ध है ?
Relevant for Exams:



