Question
A marked an article 60% above its cost price and when he
allows ‘X’% discount, he makes a profit of ________% and when he allows ‘1.5X’% discount, he make a profit of ________%. Find which of the following value/s comes in place of blank respectively. (i) 28, 12 (ii) 36, 24 (iii) 47.2, 40Solution
Let cost price be Rs.100a Marked price = 100a×160/100=Rs.160a From (i) Profit percent when he allows X% discount = 28% So, selling price = 100a×128/100=Rs.128a Value of X = (160a-128a)/160a×100=20% When he allows 1.5X% discount so, discount percentage = 1.5×20=30% New selling price = 160a×70/100=Rs.112a New profit percentage = (112a-100a)/100a×100=12% So, (i) is possible to fill the both respective fillers From (ii) Profit percent when he allows X% discount = 36% So, selling price = 100a×136/100=Rs.136a Value of X = (160a-136a)/160a×100=15% When he allows 1.5X% discount so, discount percentage = 1.5×15=22.5% New selling price = 160a×((100-22.5))/100=Rs.124a New profit percentage = (124a-100a)/100a×100=24% So, (ii) is possible to fill the both respective fillers From (iii) Profit percent when he allows X% discount = 47.2% So, selling price = 100a×147.2/100=Rs.147.2a Value of X = (160a-147.2a)/160a×100=8% When he allows 1.5X% discount so, discount percentage = 1.5×8=12% New selling price = 160a×((100-12))/100=Rs.140.8a New profit percentage = (140.8a-100a)/100a×100=40.8% So, (iii) can’t fill both respective fillers So, both (i) & (ii)
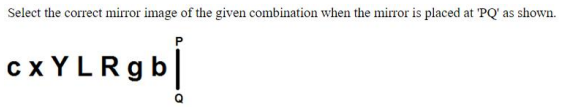
Choose the figure that is different from the rest.
Choose one of the following correct combinations of mathematical signs which can be filled to balance the following equation.
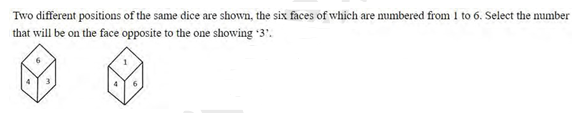
Eight boys B1, B2, B3, B4, B5, B6, B7 and B8 are sitting in a row facing towards the north (not necessarily in the same order). B6 is fifth to the right...
Find the missing number in the following number series:
22.5, ____, 26.5, 30, 34.5
Based on the alphabetical order, three of the following four letter-clusters are alike in a certain way and thus form a group. Which letter-cluster does...
In a certain code language, 'FIVE' is written as '12184410' and FOUR is written as '12304236'. How will 'THREE' be written in that language?
Select the option that is related to the fifth letter-cluster in the same way as the fourth letter-cluster is related to the third letter-cluster and th...
Select the correct mirror image of the given figure when the mirror is placed at MN.
Relevant for Exams:



