Question
A person from Pakistan residing in Karachi deceived the
complainant in Mumbai through written communication, phone calls, and telegrams, persuading them to transfer a sum exceeding five lakhs rupees to the accused's agents in Mumbai. The purpose was to facilitate the shipment of rice from Karachi to India based on their agreement. However, the promised rice was never delivered. The accused was apprehended while in England and subsequently extradited to Mumbai following legal proceedings. As per the facts stated above, state as to what offence has been committed by the accused?Solution
Explanation: Section 378. Theft—Whoever, intending to take dishonestly any movable property out of the possession of any person without that person's consent, moves that property in order to such taking, is said to commit theft. Explanation 1—A thing so long as it is attached to the earth, not being movable property, is not the subject of theft; but it becomes capable of being the subject of theft as soon as it is severed from the earth. Explanation 2—A moving effected by the same act which effects the severance may be a theft. Explanation 3—A person is said to cause a thing to move by removing an obstacle which prevented it from moving or by separating it from any other thing, as well as by actually moving it. Explanation 4—A person, who by any means causes an animal to move, is said to move that animal, and to move everything which, in consequence of the motion so caused, is moved by that animal. Explanation 5—The consent mentioned in the definition may be express or implied, and may be given either by the person in possession, or by any person having for that purpose authority either express or implied. Section 416. Cheating by personation.—A person is said to “cheat by personation” if he cheats by pretending to be some other person, or by knowingly substituting one person for or another, or representing that he or any other person is a person other than he or such other person really is. Explanation—The offence is committed whether the individual personated is a real or imaginary person. Section 420. Cheating and dishonestly inducing delivery of property—Whoever cheats and thereby dishonestly induces the person deceived to deliver any property to any person, or to make, alter or destroy the whole or any part of a valuable security, or anything which is signed or sealed, and which is capable of being converted into a valuable security, shall be punished with imprisonment of either description for a term which may extend to seven years, and shall also be liable to fine
Find the maximum value of 18 sin A + 7 cos A.
- If sin 2a = (3/2), then find the value of (sin a + cos a).
- If X = 15°, find the value of:
sin²(3X) + cos²(4X) - tan²(2X) cot 13˚
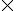 cot 14˚ ...
cot 14˚ ...If 2x = cosec @ and 4/x = cot @ then the value of 2(x ² - 1/x ² ) is
Solve for 0° ≤ θ ≤ 360°:
2 sin²θ + 3 sinθ − 2 = 0
- Simplify the following trigonometric expression:
sin 2A + sin 2B Find the value of the given expression.
2 × (sec 60° – sin 30°)
If cos θ + sin θ = m, sec θ + cosec θ = n then n(m 2 – 1) is equal to?
if x sin 45 ˚ = y cosec 30 ˚ then find the value of
Relevant for Exams:




