Question
In which of the following section of RBI Act, 1934, the
central government is empowered to constitute a six-member Monetary Policy Committee (MPC)?Solution
Under Section 45ZB of the amended (in 2016) RBI Act, 1934, the central government is empowered to constitute a six-member Monetary Policy Committee (MPC).
- Select the option in which the given figure is embedded (rotation is not allowed).
Select the option in which figure is embedded.
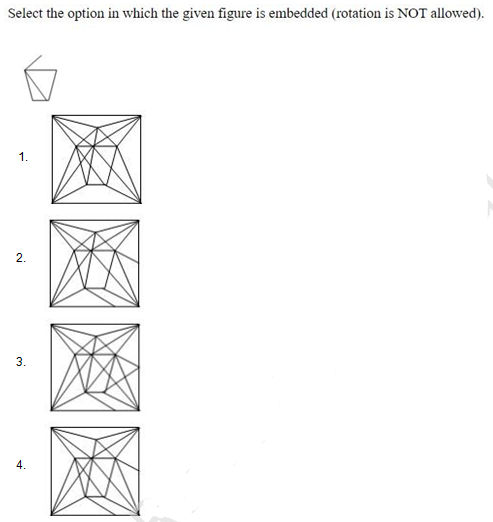
From the given answer figures, select the one in which the question figure is hidden / embedded(rotation is not allowed).
Select the option in which the given figure is embedded.
Select the option that is embedded in the given figure: (Rotation is not allowed).
Select the option in which the given figure is embedded (rotation is not allowed).
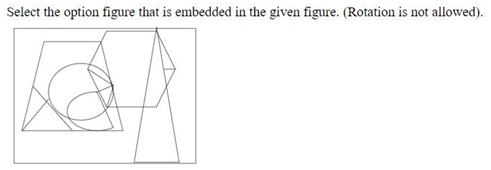
Select the option figure that is embedded in the given figure (rotation is Not allowed).
In the question, assuming the given statements to be true, find which of the conclusion (s) among given two conclusions is /are definitely true and the...



