Question
Select the most appropriate ANTONYM of the bold word.
Technology plays an indispensable role in the lives of human beings in the 21st century.Solution
The correct answer is A
Which of the following option is incorrect about “Janani Suraksha Yojana”?
Which one of the following does not figure in the list of languages in the 8th schedule of the Constitution of India?
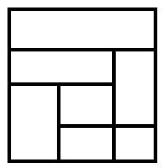
How many quadrilaterals are there in the given figure?
Which of the following statements is/are correct?
I. Jainism rose in popularity due to its simple doctrines and the use of a language understood ...
On the recommendation of which Commission, The payment of wages act 1936 Drafted?
Which of the following statements are correct about the “Lorenz Curve”?
I. The Lorenz curve is a graphic...
Among the four works mentioned below which one is encyclopaedic in nature?
Which one of the following facts pertaining to the National Green Tribunal (NGT) is not correct?
Article 243-I of the Constitution mandates setting up of the State Finance Commission (SFC) every _________ years.
The relationship between algae and fungi in Lichens is called as
Relevant for Exams:



