Question
Number of leaves considered as optimum for transplanting
rice seedlings isSolution
The correct answer is D
An interview of 60 persons to know whether they play Tennis, Chess or Carrom was conducted. The data so obtained has been summarised in a pictorial dia...
Which of the answer figure is exactly the mirror image of the question figure, when the mirror is held on the line X Y?
Which of the following diagrams best depicts the relationship between Male, Brother, Daughter.
Study the given diagram carefully and answer the question. The numbers in different sections indicate the number of persons.
Two different positions of the same dice are shown. Select the letter that will be on the face opposite to the face having the letter T?
Select the option that is related to the third figure in the same way as the second figure is related to the first figure.
Banker , Engineer, Dancer
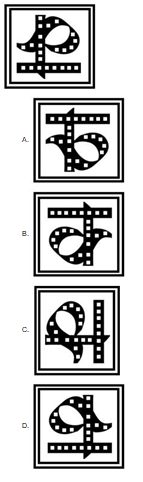
Select the correct Mirror image of the given figure.
The following Venn diagram shows the number of students who like to eat three different fruits (Dates, Mango, Cherry)
In the given figure if Triangle represents who prefer tea, Rectangle represents who prefers coffee and Circle represents who prefers soft drink then wha...



